Shrao Mehta, CEO of Secureframe, outlines six bad habits security teams must break to prevent costly and risky breaches, ransomware attacks, and prevent phishing-based endpoint attacks.
Cybercrime is on the rise and attacks are becoming faster, more sophisticated and more sophisticated. The number of data breaches related to cyber attacks increased by 27% in 2021, an upward trend that shows no signs of abating.
Kaspersky security experts have discovered a new malware that targets Microsoft Exchange servers belonging to several organizations around the world.
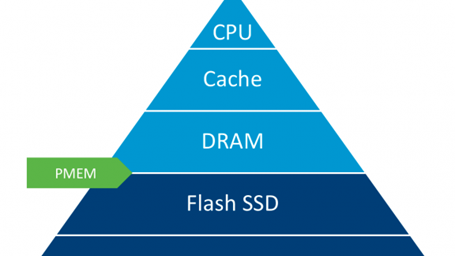
Persistent Memory technology was introduced to the market by Intel and HPE with the aim of increasing the capability of processing equipment in third generation data centers. The idea of combining the storage speed of DRAM technology with the stability of disk information makes this technology an ideal solution for storing and processing large amounts of data at a speed [...]
Introduction Today, there are few organizations and service providers around the world that have not been attacked or threatened by ransomware cyber attacks. This is directly related to the importance of information and its extent, especially with the growing increase in the production and storage of information as a result of the expansion of the use of patterns [...]
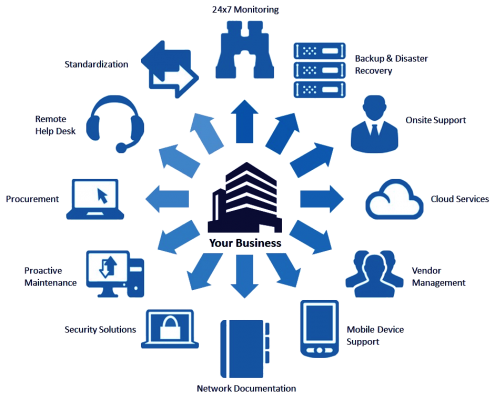
What is a Security Operations Center (SOC)? With the increasing use of information technology in all aspects of personal and social life, a large amount of commercial and administrative exchanges are carried out through the transfer of information on the Internet and other computer networks. Increasing the value of data and information resources of organizations and departments and consequently increasing attacks [...]
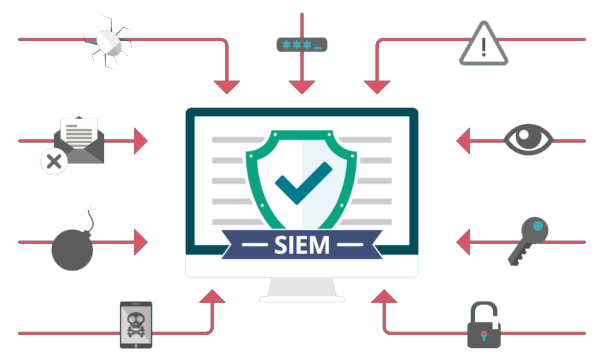
The characteristics of new generation SIEMs are early detection, rapid response and collaboration are requirements to overcome today's advanced threats. But these requirements are heavy demands on a security team. Today, monitoring and reporting on security logs and events is no longer enough, and security professionals have a broader view of all data sources in […]
Use social networks safely in your business? Considering that more than 40% of the world's population use social media and create and send several petabytes of digital content daily on social networks, it should not be surprising that these media become a frequent target for security criminals. The results of a survey that […]
Comparing SIEM and Log Management, feel the difference. Cyber threats have been increasing for the past few years, and having a log management system (Log Management) does not solve these growing cyber threats. This is where integrated tools such as SIEM come into the picture. In this article we will discuss the difference between SIEM and log management […]
Why do you still need penetration testing in 2020? The answer is simple, because you need a secure network and your network is a moving target. A penetration test can give you a real-time report of the overall security situation along with a real-time check; Can […]
Introducing Disaster Recovery Solutions Disaster Recovery includes the processes, policies and procedures necessary to provide the ability to recover operations and continue critical functions of the organization after the incident. Issues and issues such as physical damage and damages, hacking and penetration attempts, the presence of malicious computer software and emergency situations in the category [...]
- 1
- 2