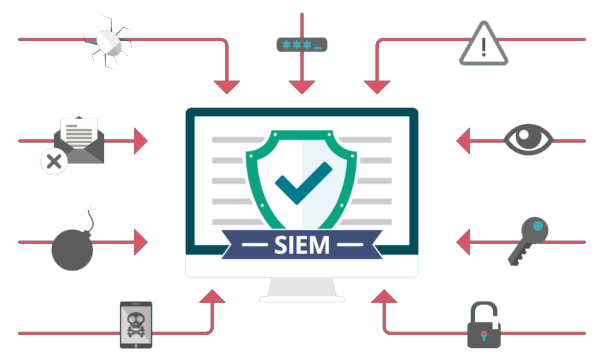
What is a Security Operations Center (SOC)? With the increasing use of information technology in all aspects of personal and social life, a large amount of commercial and administrative exchanges are carried out through the transfer of information on the Internet and other computer networks. Increasing the value of data and information resources of organizations and departments and consequently increasing attacks [...]
The characteristics of new generation SIEMs are early detection, rapid response and collaboration are requirements to overcome today's advanced threats. But these requirements are heavy demands on a security team. Today, monitoring and reporting on security logs and events is no longer enough, and security professionals have a broader view of all data sources in […]
Comparing SIEM and Log Management, feel the difference. Cyber threats have been increasing for the past few years, and having a log management system (Log Management) does not solve these growing cyber threats. This is where integrated tools such as SIEM come into the picture. In this article we will discuss the difference between SIEM and log management […]