Kaspersky security experts have discovered a new malware that targets Microsoft Exchange servers belonging to several organizations around the world.
Dubbed SessionManager and first spotted by the company in early 2022, the backdoor allows threat actors to "maintain permanent, update-resistant and relatively covert access to a targeted organization's IT infrastructure." ».
According to Kaspersky, once released, SessionManager enables a wide range of malicious activities, from email harvesting to complete control over the victim's device or infrastructure.
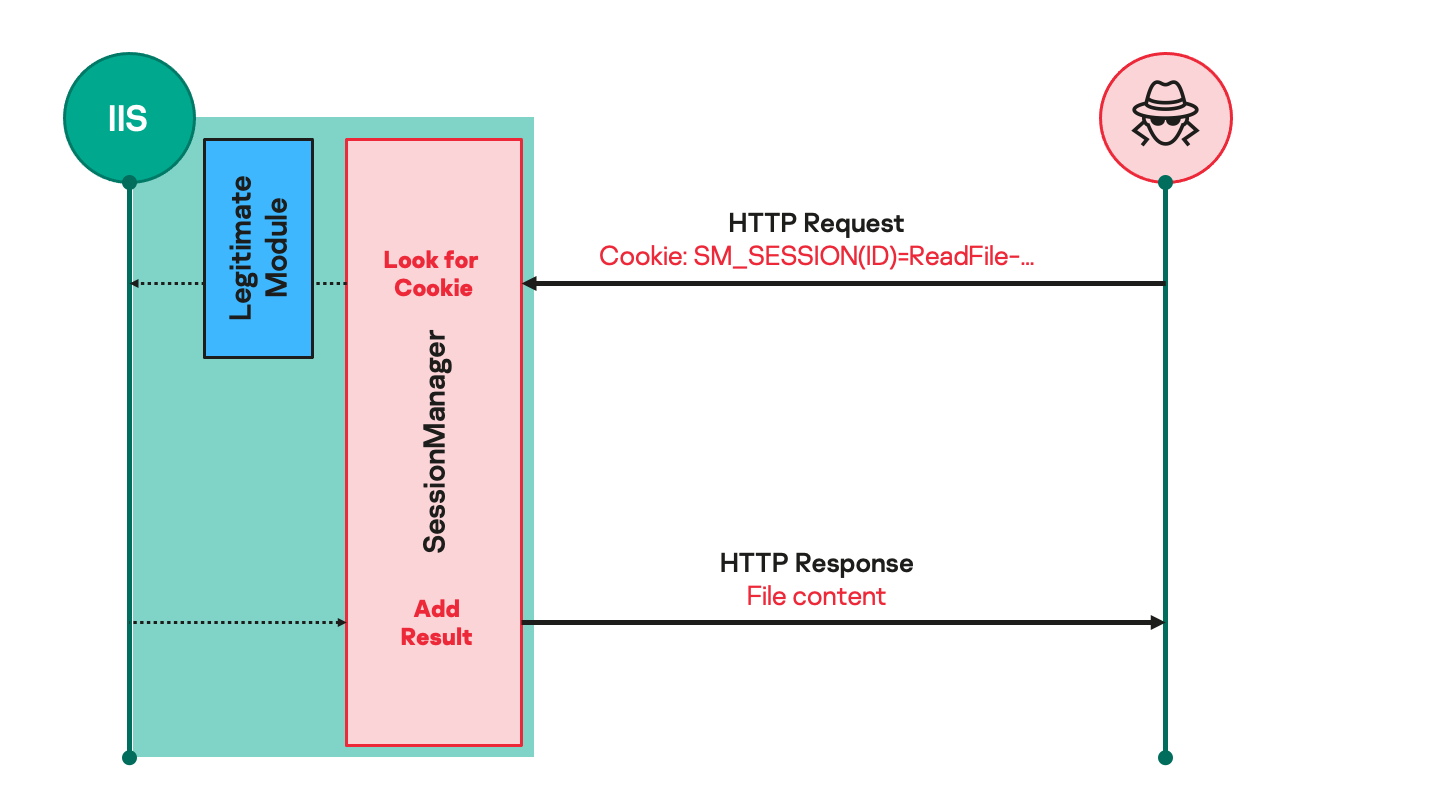
Analysis by security researchers shows that the threat actors (TA) behind SessionManager first started working in late March 2021.
Kaspersky said the malware hit 34 servers at 24 organizations across Africa, South Asia, Europe and the Middle East, most of which remain vulnerable to date.
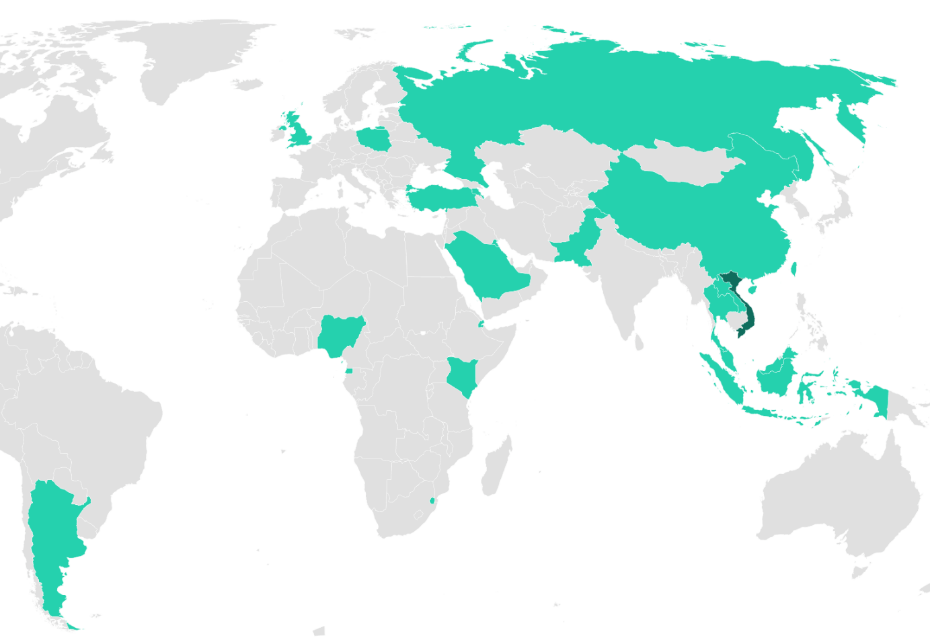
"The threat actor running SessionManager shows particular interest in NGOs and government entities, but medical organizations, oil companies, and transportation companies are among those targeted. »
Kaspersky also warned that one of the distinguishing features of SessionManager is its poor detection rate by antivirus software.
"This backdoor was first discovered by Kaspersky researchers in early 2022 when some examples of the backdoor had not yet been detected as malicious by most popular online file scanning services," the company wrote in a security advisory Thursday. »
To date, SessionManager is still deployed in more than 90 percent of target organizations, according to an Internet scan conducted by Kaspersky researchers.
Security experts said they found similarities between SessionManager and Owowa, a previously unknown Internet Information Services (IIS) module that stole user-entered credentials when logging into Outlook Web Access (OWA).
"It has become clear that deploying a backdoor in IIS is a trend for threat actors who previously exploited one of the 'ProxyLogon-type' vulnerabilities in Microsoft Exchange servers," Kaspersky wrote. »
Because of these similarities and the use of the common "OwlProxy" variant, Kaspersky concluded its recommendations by claiming that the malicious IIS module may have been exploited by the Gelsemium threat agent.
