WHAT IS THE SECURITY OPERATIONS CENTER (SOC)?
WHAT IS THE SECURITY OPERATIONS CENTER (SOC)?
With the increasing use of information technology in all aspects of personal and social life, a large amount of commercial and administrative exchanges are carried out through the transfer of information on the Internet and other computer networks. The increase in the value of data and information resources of organizations and departments and as a result the increase in internet attacks has caused the category Security in the network platform be of great importance. Therefore, using a solution to manage and secure the network in an intelligent way is one of the necessities of every organization. Security Operations Center , a place for 24-hour monitoring and control Information security The input and output to an organization is aimed at detecting security threats. The security operation center relies on a set of hardware and software equipment to collect reports of systems and services. Network securityCommunication systems, operating systems, different software and also different equipment Security and then analyze them by homogenizing and combining different reports and using advanced software and hardware and specialists. This system is able to prevent the penetration of hackers, malware and security threats from internal and external sources.
Security Operations CenterA place for 24-hour monitoring and control of the security of information entry and exit in the area of information exchange with a diagnosis attitude Security Threats Is. Security Operations Center It is a place to receive security reports from all the equipment in the network along with the analysis of the events in the network and finally to adopt security measures and apply security policies on different parts of the information exchange space. The analysis process includes the physical layer of an information system to its highest level, which is applications. Security Operations Center Relying on a set of hardware and software equipment, he collected reports of security systems and services of communication networks, operating systems, various software and also various network security equipment, and then by homogenizing and integrating various reports and using advanced software and hardware. And experts analyze them. This system, which has automatic monitoring mechanisms of network equipment, hardware and software, is able to prevent the penetration of hackers, malware and security threats through internal and external sources.
There are usually two types of companies: first, companies that have been attacked, and second, those that have been attacked and don't know yet.
In general, create a center SOC It has exorbitant costs for the organization, but if there is a need to justify the budget SOC In an organization, the following questions can be asked that focus on security threats.
How to identify a threat?
How dangerous can a threat be?
How much can a threat affect your organization?
Who is responsible for detecting and responding to a successful attack?
When an attack occurs, who should be notified and when should a threat be countered?
How and when should one engage in countering a threat, whether through internal force or through external force, and is this engagement recommended in the first place?
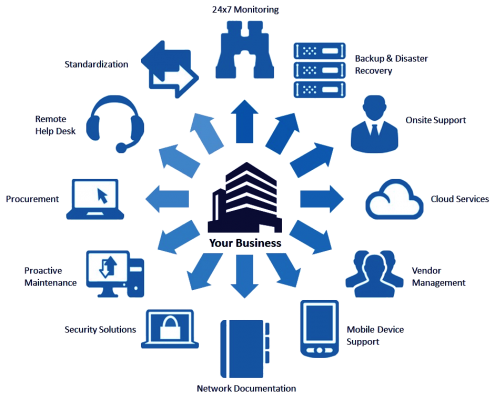
using Security Operations Center It brings the following benefits to the organization:
- Process control: streamlining and standardizing current processes at the organization level by implementing the ISO/IEC27001 standard.
- Show status Security : Displaying the security status of all devices in the network in real time.
- Vulnerability assessment: detection of network equipment vulnerabilities, reporting of vulnerable points before a security incident occurs.
- Identify, control and manage threats: manage attacks and security events, intelligently control and analyze threats using reports.
- Notification of problems: Notification of problems and notifications using SMS and follow up of problems until they are fully resolved.
- Management of security equipment: management of all network equipment centrally using SSH and Telnet protocols.
- Reporting system: providing comprehensive and diverse reports of the situation Network security to upstream managers.